Updates
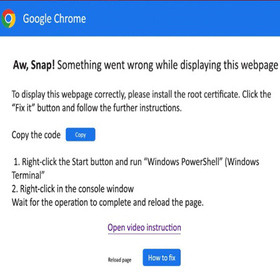
Fake Error Messages
Cybercriminals create fake error messages to lure users into installing malware while web browsing or opening a document. The errors may use convincing branding and content. Since the messages appear legitimate and offer a way to fix a problem, the user may be inclined to follow the directions.
Zombie Apps & Accounts
Zombie apps and accounts are forgotten online services that endanger your privacy, clutter your phone, and drain your battery. Your information is likely in apps, websites, and services you’ve long forgotten about. Having your email address, password, and name littered across the internet makes you a prime target for hackers. Take the time to eliminate zombie apps and dormant accounts.
Free Digital Offerings
Are you tempted to install “free” software from the internet? Have you considered the hidden cost you pay for free apps, social media, toolbars, search engines and other digital offerings that look too good to pass up?
Dumpster Diving
Dumpster diving is searching someone’s trash for information that can be used to launch a social engineering and/or computer system attack.
Typosquatting
Typosquatting targets internet users who incorrectly type a URL into their web browser.
Online Donations
It is easier than ever to support the charity of your choice with online donations. It is also easier than ever for scammers to masquerade as a charity and take advantage of those who want to help in a disaster. Spotting fake charity campaigns can be difficult.
Multi-Factor Fatigue
A cyberattack gaining in popularity is “multi-factor fatigue,” which describes incessant fraudulent push notifications sent to the owner of a compromised account.
Bluebugging
Bluebugging occurs when a hacker exploits a vulnerability or weakness in a Bluetooth connection. They accomplish this through tools and software that can detect Bluetooth devices in proximity with vulnerable connections.
Deepfake
Deepfake refers to a video, photo or voice clone that is created using artificial intelligence (AI). AI can be used to replicate images, speech patterns and mannerisms to manipulate depictions of people and events. Threat actors can use this technology to spread misinformation, cause disruption, and erode trust.