Search
Child Reaches Age 26: Employee Life Events - UT Southwestern, Dallas, TX
https://www.utsouthwestern.edu/employees/hr-resources/life-events/child-age-26.html
Employees have options for a dependent child who is dropped from UT Southwestern's medical insurance at the end of the month when they turn 26.
yyyy Article Archive: Campus News - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/campus-updates/articles/year-2026/
All of the campus news for UTSW in yyyy
Now live: UTSW Service Center portal for your service request needs and more
https://www.utsouthwestern.edu/employees/campus-updates/articles/year-2025/utsw-service-center-coming-soon.html
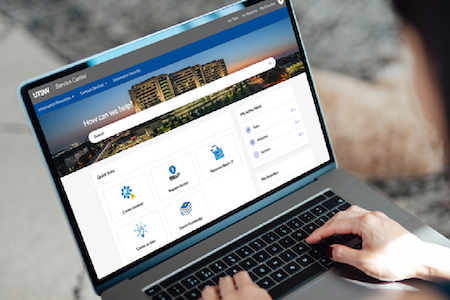
Now live: UTSW Service Center portal for your service request needs and more Published on: September 09, 2025 Share Share on Facebook Share on Twitter Share on LinkedIn Email this page Print this page The UT Southwestern Information Resources (IR) team is excited to introduce the new UTSW Service Center portal . This user-friendly portal features an enhanced ServiceNow service catalog, a robust knowledge base, and powerful search tools to help you easily request services and find the information
Working from Home Security Tips: Information Security Awareness - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/information-security/awareness/updates/work-from-home-security-tips.html

With a vast majority of the workforce working remotely, employees have an increased responsibility to protect the sensitive information they may access through the day. Here are some tips to secure your home office.
State Employee Charitable Campaign (SECC) - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/secc/?utm_source=email&utm_medium=kickoff&utm_campaign=secc25
State Employee Charitable Campaign (SECC) Your gift. Your cause. Your impact. At UT Southwestern, giving back isn’t just something we do – it’s who we are. One of the ways we do this is through the State Employee Charitable Campaign (SECC). This giving initiative empowers you to support causes close to your heart – from local groups to global humanitarian missions. Every participating organization is carefully vetted, ensuring your donation will create real and lasting impact. Anchor Link Why
Avoid geographical cyber targeting: Information Security Awareness - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/information-security/awareness/updates/avoid-geographical-cyber-targeting.html

Geo-targeted phishing occurs when cybercriminals execute customized attacks based on your geographic location.
Security tips for mobile apps: Information Security Awareness - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/information-security/awareness/updates/security-tips-for-mobile-apps.html

Some mobile apps are designed to resemble legitimate apps but instead carry out malicious activities like stealing data. Use these simple tips before you download from your device’s app store.
Free Digital Offerings: Information Security Awareness - UT Southwestern, Dallas, Texas
https://www.utsouthwestern.edu/employees/information-security/awareness/updates/free-digital-offerings-software.html

Are you tempted to install “free” software from the internet? Have you considered the hidden cost you pay for free apps, social media, toolbars, search engines and other digital offerings that look too good to pass up?
Join us in making a difference through the State Employee Charitable Campaign
https://www.utsouthwestern.edu/employees/campus-updates/articles/year-2024/secc-evp-2024.html

executive message about SECC
Flu shots for the 2024-25 flu season
https://www.utsouthwestern.edu/employees/campus-updates/articles/year-2024/flu-shots-2024.html

Flu shots for 2024-25 flu season
